Site permissions Personal Choice Some sites will ask permission to use your microphone or video camera, and the Edge browser remembers this. If you clear this option, the browser will prompt you again for access the next time you visit; it's safe to clear this option. Change a trusted location. Click File Options. Click Trust Center Trust Center Settings Trusted Locations. In the Trusted Locations list, select a location, and then click Modify. Make the modifications you want, and then click OK. Application Guard for Office. Microsoft security help and training.
In some cases, such as enterprise, have to add trusted site to group policy manually before visiting the website. Today, we'll show you how to solve this issue. Although you are new to use group policy, worry not, this tutorial is easy for you to understand.
- Open the Control Panel. Click or double-click the Internet Options icon. In the Internet Properties window, click the Security tab. Select the Trusted sites entry and click the Sites button.
- Jan 30, 2020 Internet Explorer and Legacy Edge use a system of five Zones and 88+ URLActions to make security decisions for web content, based on the host of a target site. Chromium (New Edge, Chrome) uses a system of Site Lists and permission checks to make security decisions for web content, based on the host of a target site.
- Microsoft Teams, Skype for Business Online; In this article Symptoms. When you try to sign in to Microsoft Teams in Microsoft Edge, Internet Explorer or Google Chrome, the site continually loops, and you can never sign in. This issue occurs if your organization uses Trusted Sites in Internet Explorer and doesn't enable the URLs for.
Note: Windows 10 Home edition doesn't support group policy.
How to Add Trusted Site to Group Policy Windows 10
Trusted Sites Microsoft Edge Free
Step 1: Press Windows + R key combination to invoke Run dialog. Input gpedit.msc to the box and click on OK.
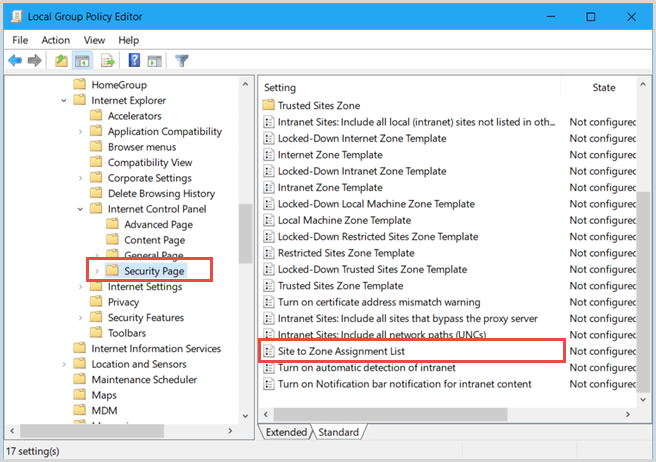
Step 2: In the left pane, navigate to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security page. Double-click on Site to Zone Assignment List in the right pane.
Step 3: In the Site to Zone Assignment List window, select Enabled then tap on Show button under Options.
Step 4: In the column under Value name, input the website. Then Type 2 in the box next to it.
Tips: Internet Explorer includes four safe zones, respectively, one to four. To add trusted site to group policy, we have to select number 2.
1: Intranet zone
2: Trusted Sites zone
3: Internet zone
4: Restricted Sites zone
Trusted Sites Microsoft Edge Gpo
Step 5: Go back to Site to Zone Assignment List window, tap on Apply then OK.
Step 6: When you finished the steps above, go to the desktop and check whether added successfully or not. Click on Search box then input Internet Explorer. Hit Enter, it will be opened at once.

Step 7: Click the gear icon in the top-right corner then select Internet options.

Step 8: Click on Security tab, tap on Trusted sites and click on Sites button.
Step 9: In the Trusted sites dialog, you will see the trusted site that added to group policy.
Related Articles:
-->Applies to:
- Windows 10
- Windows 10 Mobile
Microsoft Defender SmartScreen works with Intune, Group Policy, and mobile device management (MDM) settings to help you manage your organization's computer settings. Based on how you set up Microsoft Defender SmartScreen, you can show employees a warning page and let them continue to the site, or you can block the site entirely.
See Windows 10 (and later) settings to protect devices using Intune for the controls you can use in Intune.
Group Policy settings
SmartScreen uses registry-based Administrative Template policy settings.
| Setting | Supported on | Description |
|---|---|---|
| Windows 10, version 2004: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenExplorerConfigure Windows Defender SmartScreen | Windows 10, version 1703: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenExplorerConfigure Windows Defender SmartScreen Windows 10, Version 1607 and earlier: | This policy setting turns on Microsoft Defender SmartScreen. If you enable this setting, it turns on Microsoft Defender SmartScreen and your employees are unable to turn it off. Additionally, when enabling this feature, you must also pick whether Microsoft Defender SmartScreen should Warn your employees or Warn and prevent bypassing the message (effectively blocking the employee from the site). If you disable this setting, it turns off Microsoft Defender SmartScreen and your employees are unable to turn it on. If you don't configure this setting, your employees can decide whether to use Microsoft Defender SmartScreen. |
| Windows 10, version 2004: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenExplorerConfigure App Install Control | Windows 10, version 1703: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenExplorerConfigure App Install Control | This policy setting is intended to prevent malicious content from affecting your user's devices when downloading executable content from the internet. This setting does not protect against malicious content from USB devices, network shares, or other non-internet sources. Important: Using a trustworthy browser helps ensure that these protections work as expected. |
| Windows 10, version 2004: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenMicrosoft EdgeConfigure Windows Defender SmartScreen (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsConfigure Microsoft Defender SmartScreen (Microsoft Edge version 77 or later) Windows 10, version 1703: Administrative TemplatesMicrosoft EdgeSmartScreen settingsConfigure Microsoft Defender SmartScreen (Microsoft Edge version 77 or later) Windows 10, Version 1607 and earlier: | Microsoft Edge on Windows 10 or later | This policy setting turns on Microsoft Defender SmartScreen. If you enable this setting, it turns on Microsoft Defender SmartScreen and your employees are unable to turn it off. If you disable this setting, it turns off Microsoft Defender SmartScreen and your employees are unable to turn it on. If you don't configure this setting, your employees can decide whether to use Microsoft Defender SmartScreen. |
| Windows 10, version 2004: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenMicrosoft EdgePrevent bypassing Windows Defender SmartScreen prompts for files (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing of Microsoft Defender SmartScreen warnings about downloads (Microsoft Edge version 77 or later) Windows 10, version 1703: Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing of Microsoft Defender SmartScreen warnings about downloads (Microsoft Edge version 77 or later) Windows 10, Version 1511 and 1607: | Microsoft Edge on Windows 10, version 1511 or later | This policy setting stops employees from bypassing the Microsoft Defender SmartScreen warnings about potentially malicious files. If you enable this setting, it stops employees from bypassing the warning, stopping the file download. If you disable or don't configure this setting, your employees can bypass the warnings and continue to download potentially malicious files. |
| Windows 10, version 2004: Administrative TemplatesWindows ComponentsWindows Defender SmartScreenMicrosoft EdgePrevent bypassing Windows Defender SmartScreen prompts for sites (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing Microsoft Defender SmartScreen prompts for sites (Microsoft Edge version 77 or later) Windows 10, version 1703: Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing Microsoft Defender SmartScreen prompts for sites (Microsoft Edge version 77 or later) Windows 10, Version 1511 and 1607: | Microsoft Edge on Windows 10, version 1511 or later | This policy setting stops employees from bypassing the Microsoft Defender SmartScreen warnings about potentially malicious sites. If you enable this setting, it stops employees from bypassing the warning, stopping them from going to the site. If you disable or don't configure this setting, your employees can bypass the warnings and continue to visit a potentially malicious site. |
| Administrative TemplatesWindows ComponentsInternet ExplorerPrevent managing SmartScreen Filter | Internet Explorer 9 or later | This policy setting prevents the employee from managing Microsoft Defender SmartScreen. If you enable this policy setting, the employee isn't prompted to turn on Microsoft Defender SmartScreen. All website addresses that are not on the filter's allow list are sent automatically to Microsoft without prompting the employee. If you disable or don't configure this policy setting, the employee is prompted to decide whether to turn on Microsoft Defender SmartScreen during the first-run experience. |
| Administrative TemplatesWindows ComponentsInternet ExplorerPrevent bypassing SmartScreen Filter warnings | Internet Explorer 8 or later | This policy setting determines whether an employee can bypass warnings from Microsoft Defender SmartScreen. If you enable this policy setting, Microsoft Defender SmartScreen warnings block the employee. If you disable or don't configure this policy setting, the employee can bypass Microsoft Defender SmartScreen warnings. |
| Administrative TemplatesWindows ComponentsInternet ExplorerPrevent bypassing SmartScreen Filter warnings about files that are not commonly downloaded from the Internet | Internet Explorer 9 or later | This policy setting determines whether the employee can bypass warnings from Microsoft Defender SmartScreen. Microsoft Defender SmartScreen warns the employee about executable files that Internet Explorer users do not commonly download from the Internet. If you enable this policy setting, Microsoft Defender SmartScreen warnings block the employee. If you disable or don't configure this policy setting, the employee can bypass Microsoft Defender SmartScreen warnings. |
MDM settings
If you manage your policies using Microsoft Intune, you'll want to use these MDM policy settings. All settings support both desktop computers (running Windows 10 Pro or Windows 10 Enterprise, enrolled with Microsoft Intune) and Windows 10 Mobile devices.
For Microsoft Defender SmartScreen Edge MDM policies, see Policy CSP - Browser.
| Setting | Supported versions | Details |
|---|---|---|
| AllowSmartScreen | Windows 10 |
|
| EnableAppInstallControl | Windows 10, version 1703 |
|
| EnableSmartScreenInShell | Windows 10, version 1703 |
|
| PreventOverrideForFilesInShell | Windows 10, version 1703 |
|
| PreventSmartScreenPromptOverride | Windows 10, Version 1511 and later |
|
| PreventSmartScreenPromptOverrideForFiles | Windows 10, Version 1511 and later |
|

Recommended Group Policy and MDM settings for your organization
By default, Microsoft Defender SmartScreen lets employees bypass warnings. Unfortunately, this feature can let employees continue to an unsafe site or to continue to download an unsafe file, even after being warned. Because of this possibility, we strongly recommend that you set up Microsoft Defender SmartScreen to block high-risk interactions instead of providing just a warning.
To better help you protect your organization, we recommend turning on and using these specific Microsoft Defender SmartScreen Group Policy and MDM settings.
| Group Policy setting | Recommendation |
|---|---|
| Administrative TemplatesWindows ComponentsMicrosoft EdgeConfigure Windows Defender SmartScreen (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsConfigure Microsoft Defender SmartScreen (Microsoft Edge version 77 or later) | Enable. Turns on Microsoft Defender SmartScreen. |
| Administrative TemplatesWindows ComponentsMicrosoft EdgePrevent bypassing Windows Defender SmartScreen prompts for sites (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing Windows Defender SmartScreen prompts for sites (Microsoft Edge version 77 or later) | Enable. Stops employees from ignoring warning messages and continuing to a potentially malicious website. |
| Administrative TemplatesWindows ComponentsMicrosoft EdgePrevent bypassing Windows Defender SmartScreen prompts for files (Microsoft Edge version 45 and earlier) Administrative TemplatesMicrosoft EdgeSmartScreen settingsPrevent bypassing of Microsoft Defender SmartScreen warnings about downloads (Microsoft Edge version 77 or later) | Enable. Stops employees from ignoring warning messages and continuing to download potentially malicious files. |
| Administrative TemplatesWindows ComponentsFile ExplorerConfigure Windows Defender SmartScreen | Enable with the Warn and prevent bypass option. Stops employees from ignoring warning messages about malicious files downloaded from the Internet. |
| MDM setting | Recommendation |
|---|---|
| Browser/AllowSmartScreen | 1. Turns on Microsoft Defender SmartScreen. |
| Browser/PreventSmartScreenPromptOverride | 1. Stops employees from ignoring warning messages and continuing to a potentially malicious website. |
| Browser/PreventSmartScreenPromptOverrideForFiles | 1. Stops employees from ignoring warning messages and continuing to download potentially malicious files. |
| SmartScreen/EnableSmartScreenInShell | 1. Turns on Microsoft Defender SmartScreen in Windows. Requires at least Windows 10, version 1703. |
| SmartScreen/PreventOverrideForFilesInShell | 1. Stops employees from ignoring warning messages about malicious files downloaded from the Internet. Requires at least Windows 10, version 1703. |

Related topics
